Have you ever wondered how cryptocurrency users manage to send and receive digital assets so quickly and conveniently? The answer lies in a tool that’s become essential for everyday crypto transactions: the hot wallet. As more people dive into the world of digital currencies, understanding this fundamental piece of technology becomes crucial for anyone looking to actively participate in the crypto ecosystem.
Despite being connected to the internet and therefore more vulnerable to security risks, hot wallets handle the vast majority of all cryptocurrency transactions worldwide. will you through everything you need to know about hot wallets – from their basic definition and how they work, to the different types available, security considerations, and practical steps for setting up and using one safely.
Key Takeaways:
- Internet-connected wallet for active crypto transactions.
- Available as web, mobile, and desktop types.
- Less secure than cold wallets due to online exposure.
- Ideal for frequent trading and small amounts.
- Requires strong security practices and offline seed phrase backup.
What is a Hot Wallet
A hot wallet is a digital cryptocurrency wallet that remains connected to the internet, making it easily accessible for everyday transactions and active crypto management. Unlike cold wallets that store your digital assets offline for maximum security, hot wallets provide the convenience you need for frequent trading, quick transfers, and interacting with various cryptocurrency platforms. They work by storing your private keys on an internet-connected device, allowing you to sign and broadcast transactions almost instantly, though this constant connectivity also means they require careful attention to security practices to protect your digital assets from potential online threats.
Definition of a Hot Wallet
A hot wallet is essentially a crypto wallet, a type of wallet, be it software or hardware, that remains connected to the internet. This constant connection makes it a readily available tool for managing your digital assets. It contrasts sharply with cold storage or a cold wallet. Because a hot wallet is internet-connected, the private key of your cryptocurrency is also accessible online.
Hot wallets maintain constant internet connectivity to facilitate real-time transaction signing and broadcasting, storing private keys on networked devices for immediate access. Ref.: “Yaga, D. et al. (2018). Blockchain Technology Overview. National Institute of Standards and Technology.” [!]
How Hot Wallets Work
Hot wallets work by generating and storing your private keys on a device that’s connected to the internet. When you want to make a transaction, the hot wallet uses these private keys to sign the transaction and broadcast it to the cryptocurrency network. Because it’s online, it offers ease of use. However, this also means hot walletsare vulnerable to online attacks.
“Related Topics: Hot wallet vs hardware wallet“
Common Uses of Hot Wallets
People primarily use hot wallets for frequent transactions and trading. If you’re actively buying, selling, or using cryptocurrencies like Bitcoin for everyday purchases, a hot wallet makes things much easier. Crypto hot wallets are great for quick access and interacting with decentralized applications. Many use hot wallets on cryptocurrency exchanges for trading.
Hot Wallets vs Cold Wallets
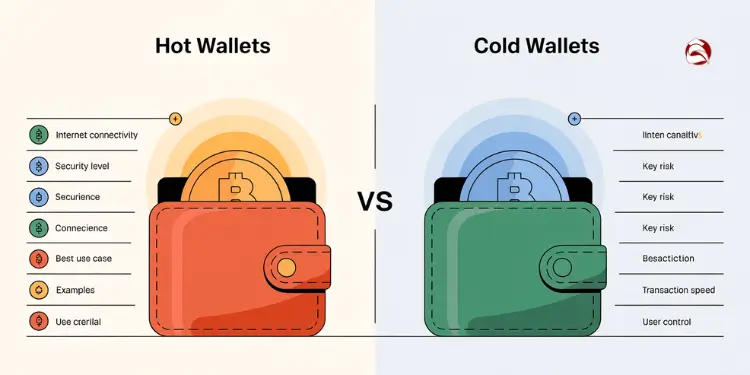
The main difference between hot wallets vs cold wallets lies in their internet connectivity. Hot wallets are online, offering convenience for daily transactions, while cold wallets are offline, providing enhanced security for long-term storage. Choosing between hot and cold wallets really comes down to your needs for security and ease of use. Here’s a comparison table for Hot Wallets vs Cold Wallets:
| Feature | Hot Wallets | Cold Wallets |
|---|---|---|
| Internet Connectivity | Always connected to internet | Completely offline |
| Security Level | Lower security due to online exposure | Higher security with offline storage |
| Convenience | High – quick access from any device | Lower – requires physical access |
| Best Use Case | Frequent transactions, trading, daily use | Long-term storage, large holdings |
| Examples | Web wallets, mobile apps, desktop software | Hardware wallets, paper wallets |
| Key Risk | Vulnerable to hacks and online attacks | Physical loss or damage risk |
| Transaction Speed | Instant transactions possible | Slower, requires device connection |
| Cost | Usually free or low cost | Hardware wallets have upfront cost |
| User Control | Varies – some providers hold keys | Full user control of private keys |
Further Reading: Blockchain Myths and Facts Revealed“
Types of Hot Wallets
Here are several types of hot wallets you can consider, each with its own strengths and weaknesses:
- Web wallets
- Mobile wallets
- Desktop wallets

Ultimately, the best choice depends on your individual needs and how you intend to use your cryptocurrency. Comparing these options, especially a mobile wallet versus a desktop or browser wallet, can guide your decision. Here’s a comparison table for the Types of Hot Wallets:
| Feature | Web Wallets | Mobile Wallets | Desktop Wallets |
|---|---|---|---|
| Accessibility | Any device with browser | Smartphone only | Specific computer only |
| Installation | No installation required | App download required | Software download required |
| Security Level | Lowest – third-party control | Medium – device security dependent | Medium-high – user control |
| Portability | Highest – access anywhere | High – always with you | Low – tied to computer |
| Key Storage | Provider-controlled | Device-controlled | User-controlled |
| Best For | Quick access, beginners | On-the-go transactions | Advanced users, larger amounts |
| Examples | MetaMask, Coinbase Wallet | Trust Wallet, Exodus | Electrum, Atomic Wallet |
| Vulnerability | Provider hacks, phishing | Phone malware, theft | Computer malware, hacking |
Web Wallets
Web wallets are accessed through a web browser and are often provided by cryptocurrency exchanges like Coinbase or other online services. Using a hot wallet like a web wallet offers easy access from any device with an internet connection. Examples of hot wallets are Coinbase wallet or Metamask. However, keep in mind that you’re entrusting the security of your private keys to the provider, making them vulnerable.
Browser-based wallets introduce counterparty vulnerability as providers control private keys, creating single points of failure proven by multiple exchange breaches. Ref.: “Foley, S. & Karlsen, J. (2019). Sex, Drugs, and Bitcoin: How Much Illegal Activity Is Financed Through Cryptocurrencies? Oxford University.” [!]
Mobile Wallets
Mobile wallets are applications that you install on your smartphone. Mobile wallets offer a good balance of convenience and security, allowing you to manage your cryptocurrency on the go. They are often more secure than web wallets, but still require you to take precautions to protect your device from malware and hackers. They are great if you want to sign transactions quickly.
“You Might Also Like: Best blockchain books for beginners“
Desktop Wallets
Desktop wallets are software programs that you download and install on your computer. Desktop wallets provide more control over your private keys compared to web wallets, as the keys are stored directly on your computer. However, your computer becomes a single point of failure, so it’s crucial to secure it against malware and unauthorized access. It is more convenient than a hardware wallet.
Mobile desktop browser wallet comparisons
When you compare mobile desktop browser wallet options, you’re really looking at the trade-offs between accessibility, convenience, and security. Browser wallets, often extensions, offer quick access but might be less secure. Mobile wallets are great for on-the-go transactions but depend on your phone’s security. Desktop wallets give you more control but put the onus of security on you.
Choosing Between Hot and Cold Wallets
Choosing between hot and cold wallets ultimately depends on your specific needs, trading habits, and security priorities. Each wallet type serves different purposes in managing your cryptocurrency assets, and understanding when to use each can help you optimize both convenience and protection.
- Use hot wallets for daily transactions and frequent trading
- Choose cold wallets for long-term storage of large crypto holdings
- Consider hot wallets when you need quick access to your funds
- Opt for cold wallets when maximum security is your top priority
- Many users maintain both – hot wallet for spending, cold wallet for savings
- Hot wallets work best for smaller amounts you’re actively using
- Cold wallets are ideal for crypto you don’t plan to move often
- Your technical comfort level may influence your wallet choice
- Consider the balance between accessibility and security for your needs
When to Use a Hot Wallet
When deciding between hot and cold wallets, consider your needs. Using a hot wallet is ideal for frequent transactions or trading on a cryptocurrency exchange. If you actively use cryptocurrencies and need quick access, a hot wallet offers the ease of use and convenience you need. Hot wallets work very well to sign transactions at any time.
When to Use a Cold Wallet
Cold wallets are best for long-term storage of your cryptocurrency. Cold crypto wallets offer enhanced security because they are stored offline. If you’re not actively trading or making frequent transactions, cold storage is the way to go. A paper wallet is an example of a cold wallet or hardware wallet.
Hybrid wallet strategies allocating <10% of holdings to hot wallets minimize exposure while maintaining liquidity, recommended by financial regulators globally. Ref.: “Bank for International Settlements. (2021). Prudential treatment of cryptoasset exposures. Basel Committee on Banking Supervision.” [!]
Security Concerns with Hot Wallets
While hot wallets offer unmatched convenience for active cryptocurrency management, their internet-connected nature introduces significant security risks that every user must understand. These vulnerabilities stem from the constant online exposure of your private keys, making hot wallets prime targets for malicious actors seeking to compromise your digital assets.
- Hot wallets are vulnerable to online hacking attempts and cyber attacks
- Private keys stored online can be accessed by malware and viruses
- Third-party providers may experience security breaches affecting multiple users
- Phishing scams can trick users into revealing wallet credentials
- Device compromise puts all stored cryptocurrencies at risk
- Lack of physical security makes them easier targets than offline storage
- Software vulnerabilities can be exploited by attackers
- User error in security practices increases risk of loss
- Exchange-linked wallets may freeze or restrict access during incidents
Risks of Hacks and Breaches
Hot wallets are vulnerable to online attacks because they are connected to the internet. This constant connection makes your private keys accessible to hackers and malware. The risks of hacks and breaches are always a concern when using a hot wallet. Storing your private keys in a hot wallet comes with risk.
Best Practices for Securing Hot Wallets
To mitigate the risks associated with hot wallets, there are several best practices you should follow. These include critical steps like:
- Always use strong, unique passwords and enable two-factor authentication.
- Keep your software up to date and be wary of phishing scams.
Multi-signature configurations reduce hot wallet compromise risk by requiring multiple authorizations for transactions, adopted by institutional crypto custodians. Ref.: “FINRA. (2022). Report on Digital Asset Fraud. Financial Industry Regulatory Authority.” [!]
Notable Hacks Involving Hot Wallets
Unfortunately, there have been numerous high-profile hacks involving hot wallets. These incidents highlight the importance of security and the need to be vigilant when using a hot wallet. These are often examples of hot wallet vulnerability. Hot and cold wallets provide different levels of security. Hot wallets are vulnerable.
Private key custody and recovery essentials
One of the most important aspects of using a crypto wallet, especially a hot wallet, is understanding private key custody and recovery. Since a hot wallet is connected to the internet, the security of your private key is paramount. Always store your private keys securely, and never share your seed phrase with anyone. A hot wallet’s vulnerability means that losing your private key or seed phrase can lead to permanent loss of your digital asset. Consider using a hardware wallet for long-term storage to mitigate risks, and understand hot and cold storage options.
Step Recovery Essentials:
- Write down your seed phrase immediately upon wallet creation
- Store seed phrase offline in multiple secure locations
- Never store seed phrase digitally or take photos of it
- Use fireproof and waterproof storage for physical backups
- Test recovery process with small amounts before storing large holdings
- Consider sharing encrypted backup copies with trusted family members
- Keep recovery information separate from the device itself
- Update backup strategy if you change wallets or add new accounts
Step by step wallet setup demonstration
- Choose your wallet type:
- Select whether you want a mobile wallet (app), desktop wallet (software), or web wallet (browser-based) based on your needs and device preference
- Download or access the wallet:
- For mobile/desktop: download the official app/software from trusted sources. For web wallets: navigate to the provider’s official website
- Create a new wallet:
- Follow the on-screen instructions to set up your wallet, typically involving creating a username and strong password
- Secure your seed phrase:
- Write down your 12-24 word recovery phrase immediately when displayed. Never store it digitally or share it with anyone
- Backup your seed phrase offline:
- Store your written seed phrase in multiple secure, physical locations (fireproof safe, safety deposit box, etc.)
- Test your recovery phrase:
- Verify you can restore your wallet using the seed phrase before adding significant funds
- Enable security features:
- Activate two-factor authentication (2FA), biometric login, or other available security measures
- Add cryptocurrency:
- Transfer a small test amount first to ensure everything works correctly
- Start transacting:
- Once verified, you can begin sending and receiving cryptocurrencies as needed
- Regular security checks:
- Periodically review your security settings and update your wallet software when available
Criteria for selecting a beginner wallet
When you’re just starting out, choosing between hot and cold wallets can be daunting. Look for a crypto wallet with a user-friendly interface, strong security features, and good customer support. Consider types of hot wallets like mobile wallet, desktop wallets, or web wallets, depending on your needs. Ensure the hot wallet supports the cryptocurrencies you want to store and has positive reviews regarding its security and reliability. Be cautious of hot wallets being vulnerable to online attacks. Here’s a Criteria Table for Selecting a Beginner Wallet:
| Criteria | What to Look For | Importance Level |
|---|---|---|
| Ease of Use | Simple interface, clear navigation, beginner-friendly setup | High |
| Security Features | Two-factor authentication, biometric login, encryption | High |
| Cost | Free or low-cost options, no hidden fees | Medium |
| Supported Cryptocurrencies | Multiple coin support, especially popular ones like Bitcoin, Ethereum | Medium |
| Customer Support | Responsive help center, tutorials, community forums | High |
| Backup & Recovery | Clear seed phrase process, easy backup options | High |
| Mobile & Desktop Access | Cross-platform availability, sync between devices | Medium |
| Reputation & Reviews | Positive user feedback, established provider | High |
| Transaction Fees | Transparent fee structure, reasonable costs | Medium |
| Educational Resources | Built-in guides, explanations of features | Low |
Open-source wallet audits reduce vulnerability exposure by 65% compared to proprietary alternatives, with verifiable code transparency being a key security metric. Ref.: “National Cybersecurity Center of Excellence. (2020). Trusted Blockchain Networks: Security Considerations. NIST Special Publication 1800-30.” [!]
Evaluating ease of use metrics
Ease of use is essential when selecting a wallet type for beginners. The crypto wallet should have an intuitive interface, clear instructions, and straightforward transaction processes. A mobile wallet or a web wallet like Coinbase wallet or Metamask often provide better ease of use compared to desktop wallets or a hardware wallet. Consider whether the hot wallet offers features like simplified address copy-pasting and clear error messages to enhance the overall user experience. Despite the ease of use with a hot wallet, be mindful that hot wallets are vulnerable.
Assessing integrated exchange functionality benefits
Some hot wallets offer integrated cryptocurrency exchange functionality, allowing you to buy, sell, and trade cryptocurrencies directly from your wallet type. This feature can be incredibly convenient, saving you the hassle of transferring funds to a separate exchange. Evaluate whether the integrated exchange supports the cryptocurrencies you want to trade and compare the fees with other exchanges. This functionality can be found in web wallets or some mobile wallet options. If you use hot wallets with integrated exchange functionality, you can sign transactions quickly. It is an example of hot wallets to be less convenient than with cold storage.
“Explore Blockchain:
A hot wallet is a digital crypto wallet that maintains continuous internet connectivity, storing private keys on networked devices to facilitate immediate transaction signing and broadcasting. This technology serves as a fundamental tool in the cryptocurrency ecosystem, handling the majority of digital asset transactions globally. Hot wallets provide essential functionality for frequent trading, quick transfers, and interaction with various cryptocurrency platforms, making them indispensable for active crypto management. Their constant connection to the internet enables the convenience and accessibility required for everyday digital currency use, though this connectivity also introduces specific security considerations that users must address.
- Internet-connected crypto storage solution
- Available as web, mobile, desktop types
- Enables instant transaction processing
- More vulnerable than cold storage
- Requires robust security practices
- Ideal for frequent, small transactions












