Securing digital assets requires robust solutions. Did you know multisig wallet vault configuration prevent single points of failure by requiring multiple signatures? This enhanced security mechanism protects against unauthorized access to crypto holdings.
Multisig technology distributes control across several parties, making it virtually impossible for a single compromised key to access funds. Fact: Even if one key is lost in a 2-of-3 setup, funds remain secure and accessible through the remaining keys.
What is a Multisig Wallet?

A multisig wallet requires multiple signatures to authorize transactions, enhancing security by eliminating single points of failure. Unlike traditional wallets that rely on one private key, multisig distributes control among multiple signers. This makes unauthorized access virtually impossible as no single key can move funds without approval from others.
Multi-signature wallets eliminate single points of failure by requiring multiple private keys to authorize transactions, making unauthorized access virtually impossible. Even if one key is compromised, funds remain secure as long as the threshold number of keys is not breached. Ref.: “BitPay Team. (2023). Using Multisig Wallets to Secure Your Crypto Assets. BitPay.” [!]
Benefits of Using a Multisig Vault
A multisig wallet, short for multi-signature wallet, introduces a more robust approach to managing your bitcoin balance and other crypto assets. Unlike a standard wallet that relies on a single private key to authorize transactions, a multisig wallet requires multiple approvals. This decentralizes control, mitigating the risks associated with a single point of failure. The multisig features offered by such setups ensure that no single key holder can move the funds without the consent of others.
How Multisig Works on the Blockchain
Multisig wallets operate on the blockchain by employing a smart contract that governs transaction authorization. For instance, in a 2-of-3 multisig setup, at least two private keys out of three are needed to sign and broadcast a transaction to the blockchain. Each key corresponds to a public key. This is a fundamental aspect of bitcoin multisig wallet functionality. This mechanism prevents unauthorized access and adds an extra layer of security compared to a wallet using just one key.
Traditional multisig implementations focus on requiring multiple approvals but lack mechanisms for verifying transaction legitimacy or preventing unauthorized access at deeper levels. Recent breaches demonstrate that multisig wallets are still vulnerable to signer key theft, lack of contextual verification, and blind approvals where signers don’t thoroughly review transaction contents. Ref.: “FailSafe Team. (2023). The Hidden Risks of Multisig Wallets: Lessons from Bybit, 0xInfini, and How to Stay Secure. FailSafe.” [!]
Step-by-Step Guide to Create a multisig wallet vault configuration
Creating a multisig vault requires careful planning and execution to ensure maximum security for your digital assets. This comprehensive guide walks you through each essential step, from initial configuration to ongoing management, providing the knowledge needed to implement robust multisig security for your cryptocurrency holdings.
Choosing the Right Setup for Your Wallet
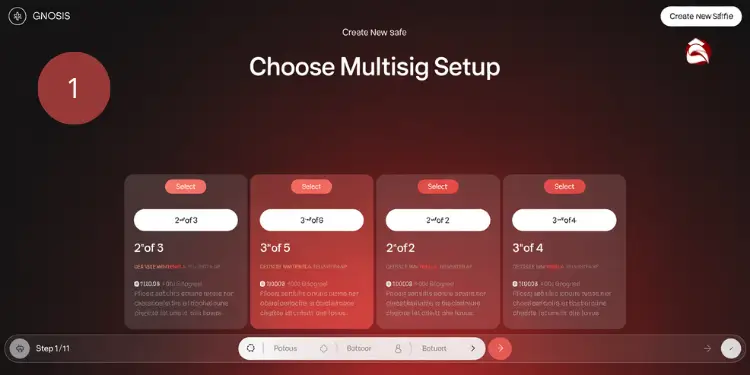
Before creating your multisig vault, selecting the appropriate configuration is crucial for balancing security and accessibility. Consider your specific use case, risk tolerance, and recovery requirements when making this decision. Common configurations include:
- 2-of-3: Requires 2 out of 3 signatures for transactions
- 3-of-5: Requires 3 out of 5 signatures for enhanced security
- 2-of-2: Requires both signatures for maximum security
- 3-of-4: Balances security with redundancy
| Configuration | Security Level | Accessibility | Best For |
|---|---|---|---|
| 2-of-3 | High | Good | Personal/SMB |
| 3-of-5 | Very High | Moderate | Enterprise |
| 2-of-2 | Maximum | Limited | High Security |
| 3-of-4 | High | Good | Teams |
Creating a 2-of-3 Multisig Vault
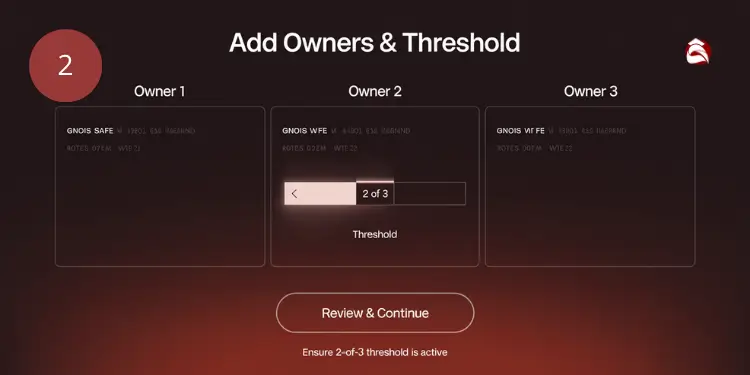
The 2-of-3 multisig setup is widely adopted for its optimal balance of security and usability. This configuration requires any two of three private keys to authorize transactions, providing both security and redundancy. To create a 2-of-3 multisig vault, follow these steps:
- Select compatible wallet software:
- Sparrow Wallet (Bitcoin-only)
- Gnosis Safe (Ethereum-based assets)
- Electrum (Bitcoin support)
- Casa (Multi-asset support)
- Generate three unique private keys:
- Create keys on separate devices
- Ensure each key is securely backed up
- Distribute keys among trusted parties
- Configure wallet parameters:
- Set signature requirement to 2-of-3
- Define transaction limits
- Configure recovery procedures
Utilizing Hardware Wallets for Enhanced Security
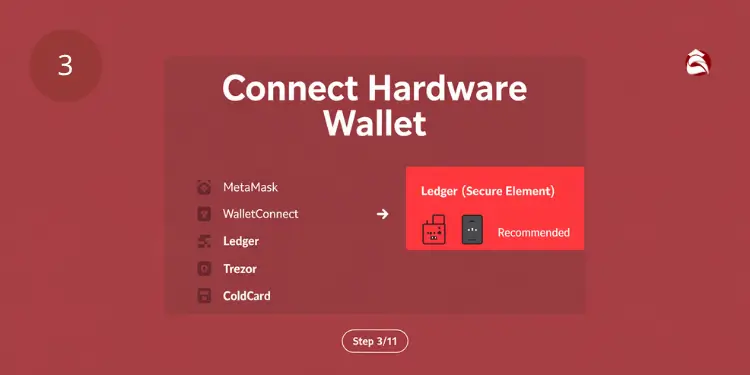
Hardware wallets provide the highest level of security for multisig setups by keeping private keys offline and protected from online threats. Integrating hardware devices into your multisig configuration is essential for enterprise-grade security. Recommended hardware wallets:
- Ledger: Multi-asset support, user-friendly interface
- Trezor: Open-source, strong security features
- Coldcard: Bitcoin-focused, air-gapped capabilities
- KeepKey: Simple design, multi-asset support
| Hardware Wallet | Security Features | Supported Assets | Price Range |
|---|---|---|---|
| Ledger | Secure Element, PIN | 1000+ | $79-$279 |
| Trezor | Open Source, Passphrase | 1000+ | $69-$279 |
| Coldcard | Air-gapped, SD Card | Bitcoin only | $149 |
| KeepKey | Large Display, PIN | 40+ | $49 |
Parameter Selection and Default Values
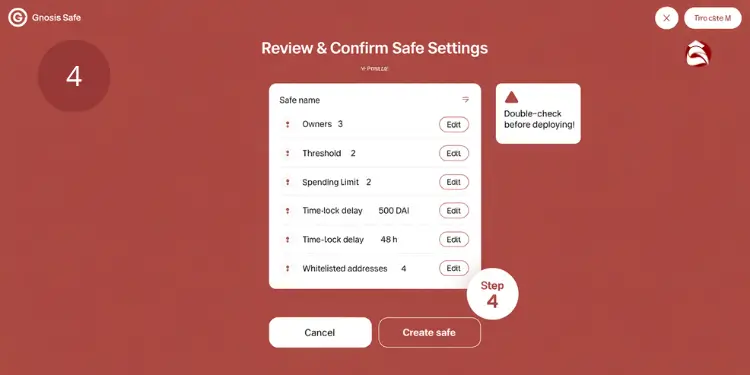
Proper parameter configuration is critical for multisig vault security and functionality. A systematic approach to parameter selection ensures optimal performance while maintaining security standards. Critical parameters to validate:
- Signature threshold: Number of required signatures
- Maximum transaction amount: Daily/weekly limits
- Time locks: Delays for large transactions
- Whitelisted addresses: Pre-approved destinations
- Recovery procedures: Key loss protocols
Threshold Tuning and Signer Management
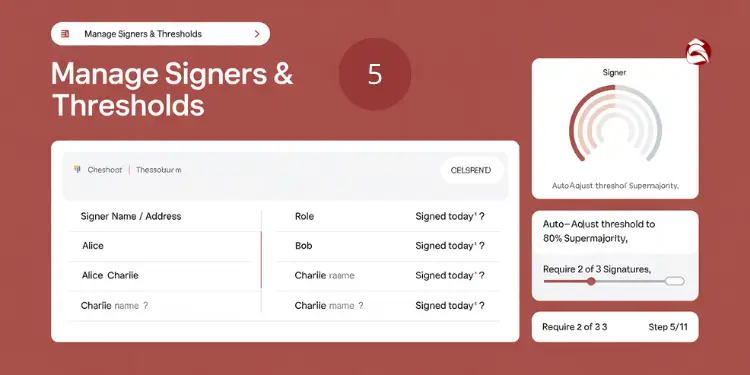
Dynamic threshold adjustment allows your multisig vault to adapt to changing security requirements while maintaining robust protection against unauthorized access. The dynamic threshold change procedure includes:
- Initiation: Proposal from authorized signers
- Security verification: Multi-factor authentication
- Voting period: Time for all signers to review
- Supermajority approval: Typically 80% or higher
- Implementation: Automatic or manual execution
“Explore More: Blockchain explained for beginners in plain English“
Signer Addition Removal Authorization Workflow
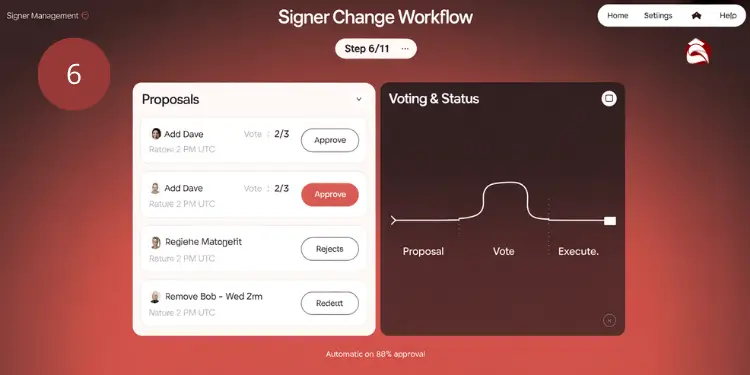
Managing signers requires a robust authorization workflow to maintain vault integrity and prevent unauthorized modifications to the multisig configuration. The signer management workflow follows this structure:
| Action | Initiation | Authorization | Implementation |
|---|---|---|---|
| Add / Remove Signer | Proposal from existing signer(s) | Voting period with predefined threshold | Automatic upon |
Emergency Override Threshold Scenario Handling
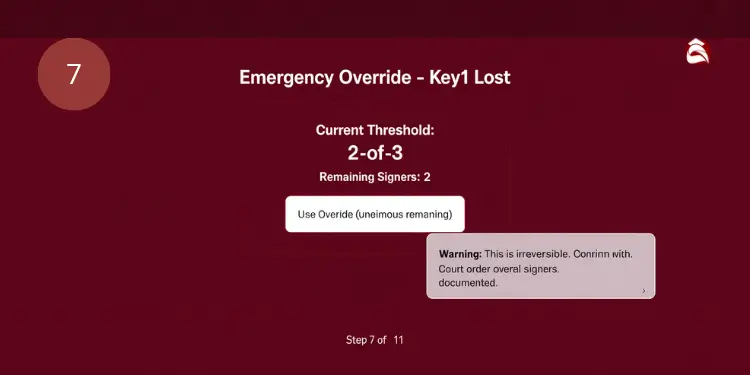
Emergency scenarios require special procedures to ensure asset accessibility while maintaining security. Proper emergency override protocols are essential for business continuity. Emergency override procedures:
- Key loss scenarios: Require unanimous remaining signer approval
- Compromised key: Immediate threshold adjustment with enhanced verification
- Natural disaster: Pre-defined emergency contacts and procedures
- Legal requirements: Court-ordered access with proper documentation
“Related Articles: How to get into blockchain entry tips for beginners“
Role Based Permissions Configuration Workflow
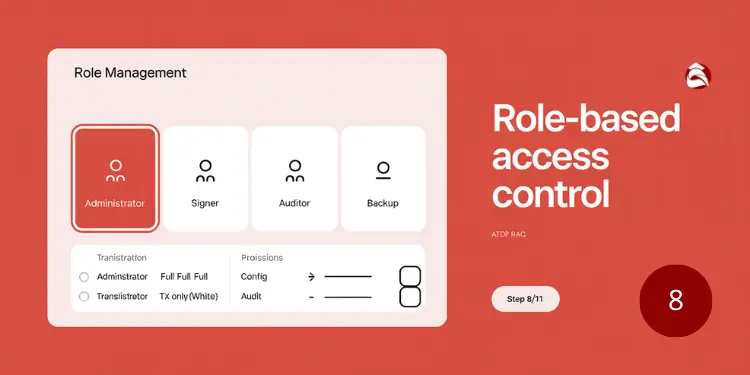
Role-based access control ensures that each participant has appropriate permissions based on their responsibilities and trust level within the organization. Common roles and permissions:
- Administrator: Full control, can modify settings
- Signer: Can authorize transactions only
- Auditor: Read-only access for monitoring
- Backup: Emergency access only
| Role | Transaction Authority | Configuration Access | Monitoring Rights |
|---|---|---|---|
| Administrator | Full | Full | Full |
| Signer | Authorized | Limited | Basic |
| Auditor | None | None | Full |
| Backup | Emergency Only | None | Basic |
Gas Optimization and Cost Controls
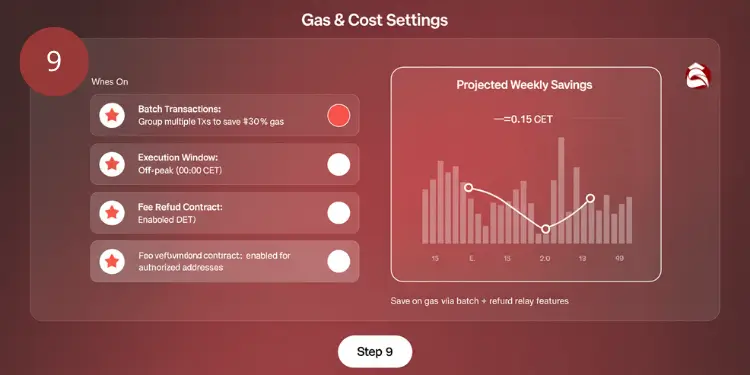
Efficient gas management is crucial for Ethereum-based multisig vaults to minimize transaction costs while maintaining security and functionality. Gas optimization strategies:
- Batch processing: Group multiple transactions
- Off-peak execution: Lower network congestion periods
- Gas price monitoring: Real-time adjustment
- Smart contract optimization: Efficient code design
Batch Transaction Bundling Strategy Plan
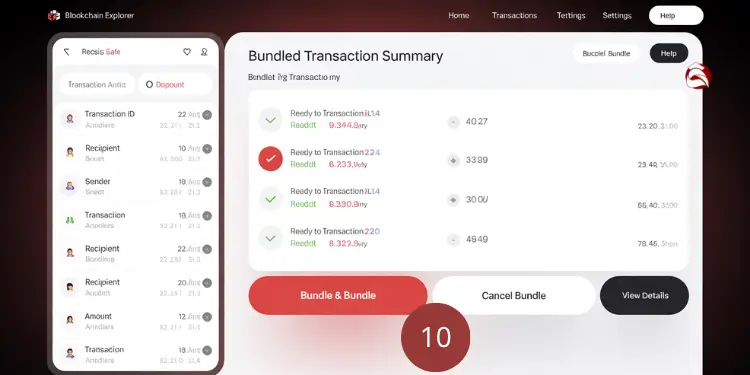
Transaction bundling significantly reduces gas costs by combining multiple operations into a single transaction, improving efficiency and reducing overall fees. Batch bundling criteria:
- Transaction type compatibility: Similar operations grouped
- Size limitations: Maximum bundle size based on gas limits
- Timing optimization: Strategic submission times
- Priority levels: High-priority transactions processed separately
Fee Refund Relay Integration Steps
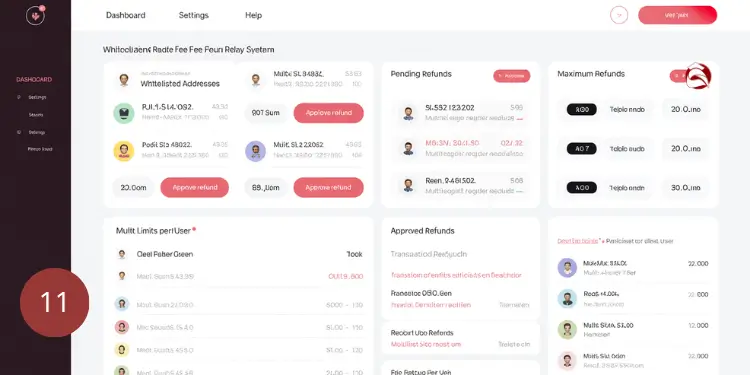
Fee refund mechanisms help manage transaction costs by providing reimbursement options for authorized users, making multisig operations more cost-effective. Integration process:
- Smart contract deployment: Fee management contract
- Address whitelisting: Authorized refund recipients
- Limit configuration: Maximum refund amounts
- Security verification: Multi-signature approval for refunds
Monitoring Hooks and Notification Integration
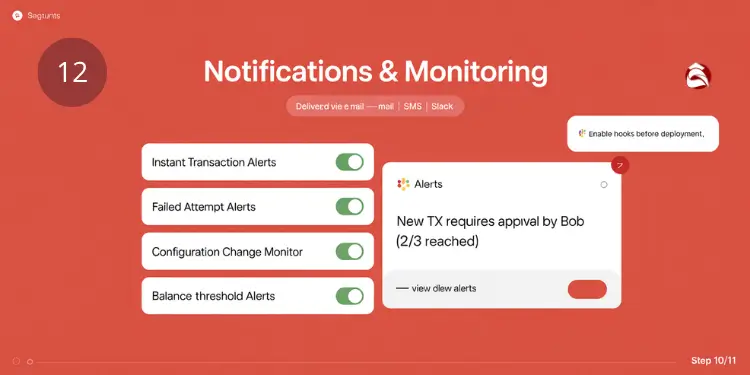
Continuous monitoring and real-time notifications are essential for maintaining multisig vault security and operational integrity. Monitoring capabilities:
- Transaction alerts: Incoming/outgoing transfers
- Failed attempts: Unauthorized access notifications
- Configuration changes: System modification alerts
- Balance monitoring: Asset level notifications
Configuration Migration and Version Tracking
Proper configuration management ensures smooth transitions between systems and maintains a complete audit trail of all changes to the multisig vault. Migration procedures:
- Environment transfer: Moving between systems
- Version control: Change tracking and documentation
- Rollback capabilities: Reverting to previous configurations
- Audit trails: Complete change history
Changelog Documentation Automation Process Guide
Automated changelog documentation ensures transparency and accountability in multisig vault management, providing a complete record of all configuration changes. Automation features:
- Automatic logging: Real-time change documentation
- Version control integration: Git-based tracking
- Change attribution: User identification and timestamps
- Audit reporting: Compliance-ready documentation
Critical variables validation checklist guide
Proper validation of critical variables is essential when configuring a multisig vault to ensure optimal security and functionality. This checklist provides a systematic approach to verifying all essential parameters, helping you establish a robust multisig setup that meets your specific security requirements while maintaining operational efficiency. Critical Variables Validation:
- Signature Threshold Configuration
- Verify M-of-N setup matches security requirements
- Confirm minimum signers required for transactions
- Validate threshold cannot be easily modified
- Transaction Authorization Parameters
- Set maximum transaction amount limits
- Configure daily/weekly spending caps
- Define whitelisted destination addresses
- Establish time lock periods for large transfers
- Security Protocol Validation
- Confirm hardware wallet integration
- Verify private key generation and storage
- Validate backup and recovery procedures
- Check multi-factor authentication requirements
- Smart Contract Settings
- Review contract code for vulnerabilities
- Verify upgrade mechanisms and restrictions
- Confirm gas optimization parameters
- Validate emergency override procedures
- Access Control Verification
- Test role-based permission assignments
- Confirm signer addition/removal workflows
- Validate administrator privilege levels
- Verify audit trail configuration
- Network and Blockchain Parameters
- Confirm blockchain network compatibility
- Verify address format requirements
- Validate transaction fee structures
- Check network-specific security features
- Compliance and Regulatory Checks
- Verify KYC/AML integration requirements
- Confirm regulatory reporting capabilities
- Validate audit trail completeness
- Check jurisdiction-specific compliance needs
Dynamic Threshold Change Procedure Guide
Dynamic threshold changes provide flexibility for multisig vaults to adapt to evolving security requirements while maintaining robust protection. This procedure ensures all modifications follow strict security protocols and require proper authorization from authorized signers.
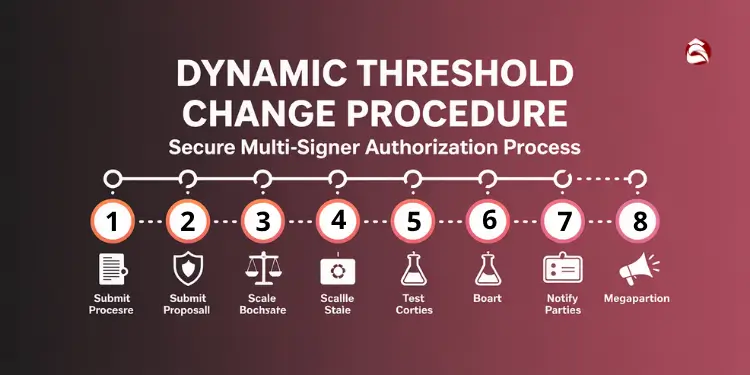
Step 1: Initiate Threshold Change Proposal
- Submit formal proposal through the multisig wallet interface
- Specify current threshold (e.g., 2-of-3) and proposed new threshold (e.g., 3-of-3)
- Include detailed justification for the change
- Set proposal expiration timeframe (typically 24-72 hours)
Step 2: Security Verification Process
- Authenticate all initiating signers with hardware wallets
- Verify digital signatures on the proposal
- Confirm proposal format meets wallet requirements
- Validate that proposed change doesn’t violate security policies
Step 3: Multi-Signer Voting Period
- Notify all authorized signers of the pending threshold change
- Allow sufficient time for review and consideration (minimum 24 hours)
- Track voting progress in real-time through wallet interface
- Maintain audit log of all votes cast
Step 4: Supermajority Approval Check
- Verify that required approval threshold is met (typically 80% or higher)
- Confirm quorum requirements are satisfied
- Validate that all approving signers are active and authorized
- Check for any objections or security concerns raised
Step 5: Implementation Execution
- Once approved, execute threshold change through smart contract
- Update wallet configuration files with new threshold settings
- Verify successful implementation across all signer devices
- Confirm new threshold is active and functioning correctly
Step 6: Post-Implementation Validation
- Test new threshold with sample transactions
- Verify all signers can operate under new configuration
- Confirm emergency procedures still function properly
- Update documentation and security protocols accordingly
Step 7: Documentation and Audit Trail
- Record complete change process in system changelog
- Document all participating signers and approval timestamps
- Archive proposal documentation and voting records
- Update compliance documentation and security policies
Step 8: Notification and Communication
- Inform all relevant stakeholders of successful threshold change
- Update emergency contact procedures if necessary
- Communicate new operational requirements to all signers
- Schedule follow-up security review within 30 days












