In the rapidly evolving world of cryptocurrency, managing digital assets securely and efficiently has become a top priority for investors and everyday users alike. Among the various storage solutions available, the hot wallet stands out as a popular choice for those who need immediate access to their funds for regular transactions.
A hot wallet is a digital wallet that remains connected to the internet, allowing users to send, receive, and manage their cryptocurrency holdings with unparalleled convenience. Unlike their offline counterparts, hot wallets provide the speed and accessibility necessary for active participation in the crypto ecosystem.
Did you know that despite their convenience, hot wallets are responsible for storing only a small fraction of the total cryptocurrency supply, with the majority of funds being held in more secure cold storage solutions? This fact highlights the critical balance between accessibility and security that every crypto user must navigate.
Key Takeaways:
- Hot wallets provide instant transaction accessibility.
- Private keys remain encrypted during storage.
- Internet connectivity increases security vulnerability.
- Multi-factor authentication enhances transaction security.
- Best for daily operational funds only.
- Combine with cold storage for optimal security.
How does hot wallet work: typical wallet transaction
When using a hot wallet for a crypto transaction, you begin by entering the recipient’s address and amount in your wallet software. The wallet then signs the transaction and submits it to the blockchain network. In seconds to minutes. the transaction is verified and completed, ensuring fast and secure transfer. The working mechanism of a hot wallet transaction operates through the following steps:
- Transaction Initiation:
You enter the recipient’s cryptocurrency address and the amount you want to send through your hot wallet interface.
- Private Key Access:

Your hot wallet securely accesses your private key, which is stored in an encrypted format within the wallet software or device.
- Digital Signature Creation:
The wallet uses private key to create a unique digital signature for the transaction, proving that you are the authorized owner of the funds being sent.
- Transaction Broadcasting:

Once signed, the transaction is broadcast to the cryptocurrency network through connected nodes, making it visible to miners or validators.
- Network Verification:

Network nodes verify the transaction’s validity by checking that you have sufficient funds and that the digital signature is authentic using your public key.
- Block Inclusion:
Validated transactions are grouped together by miners or validators into a block, which then competes to be added to the blockchain.
- Network Confirmation:
Once the block is successfully added to the blockchain, the transaction receives its first confirmation. Additional confirmations occur as more blocks are added to the chain, making the transaction increasingly secure and irreversible.
- Balance Update:
Both your wallet and the recipient’s wallet update to reflect the new balances, completing the transfer of digital assets.
Blockchain transaction verification requires consensus mechanisms like Proof-of-Work or Proof-of-Stake to prevent double-spending attacks, with validation times varying by network congestion and fee selection Ref.: “Narayanan, A. et al. (2016). Bitcoin and Cryptocurrency Technologies. Princeton University Press.” [!]
From signature creation to network confirmation
When you make a crypto transaction using a hot wallet, it signs the transaction with your private key. The signed transaction is then broadcast to the network for confirmation.
| Action | Details |
|---|---|
| Signature Creation | Hot wallet uses your private key to create a digital signature. |
| Transaction Verification | Nodes on the network verify the transaction’s validity. |
After validation, the transaction is included in a block and added to the blockchain, completing the process and confirming the transfer of digital assets.
Check out the below:
Role of private and public keys
Private and public keys are fundamental to security and authentication, especially within the context of crypto wallets. When you send cryptocurrency, your private key is used to create a digital signature that proves you authorized the transaction. The network then uses your public key to verify that the signature is valid, ensuring the transaction’s authenticity. Hot wallets offer convenience, but it’s crucial to understand how private and public keys function to protect your crypto assets.
| Key Type | Function |
|---|---|
| Private Key | Allows you to manage your crypto. It’s a secret code that allows you to sign transactions and prove ownership. |
| Public Key | Used to receive cryptocurrency. |
How hot wallets connect to blockchains
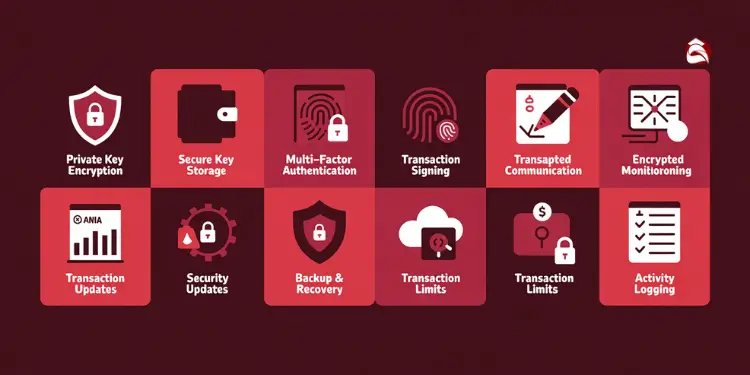
The working mechanism of hot wallet security operates through the following steps:
- Private Key Encryption: Hot wallets encrypt private keys using advanced cryptographic algorithms, ensuring they remain protected even if the device is compromised.
- Secure Key Storage: Private keys are stored in secure enclaves or hardware-backed storage areas that are isolated from the main operating system, preventing unauthorized access.
- Multi-Factor Authentication: Users must provide multiple forms of verification (password, biometric data, or authentication codes) before accessing wallet functions or authorizing transactions.
- Transaction Signing: When a transaction is initiated, the wallet creates a digital signature using the encrypted private key without exposing the actual key to potential threats.
- Network Communication Security: All communications between the wallet and blockchain nodes are encrypted using secure protocols to prevent interception or tampering.
- Transaction Monitoring: The wallet continuously monitors for suspicious activity and can flag or block unusual transaction patterns.
- Regular Security Updates: Wallet software automatically updates to patch vulnerabilities and implement the latest security enhancements.
- Backup and Recovery: Encrypted backup mechanisms ensure users can recover their wallets if devices are lost or compromised, while maintaining security through seed phrase protection.
- Transaction Limits: Optional spending limits and multi-signature requirements add additional layers of protection for large transactions.
- Activity Logging: Comprehensive logs track all wallet activities, enabling users to review and verify all transactions for unauthorized access.
Security mechanisms mitigating online threats
Hot wallets employ multiple security layers to protect digital assets from online threats while maintaining accessibility.
| Security Mechanism | Function |
|---|---|
| Private Key Encryption | Encrypts private keys using advanced cryptographic algorithms to prevent unauthorized access |
| Secure Enclaves | Stores keys in isolated, hardware-protected areas separate from the main operating system |
| Two-Factor Authentication | Requires multiple verification methods before allowing access or transaction approval |
| Transaction Limits | Imposes spending caps and multi-signature requirements for large transactions |
| Regular Updates | Automatically patches vulnerabilities and implements latest security enhancements |
| Activity Monitoring | Continuously monitors for suspicious activities and unusual transaction patterns |
Seed phrase encryption and storage options
Two factor authentication for transaction approvals
Two-factor authentication (2FA) provides an essential security layer for hot wallet transactions by requiring multiple verification forms, significantly reducing unauthorized access risks even if passwords or private keys are compromised. This standard security practice offers users peace of mind while maintaining the convenience that hot wallets provide for everyday crypto transactions.
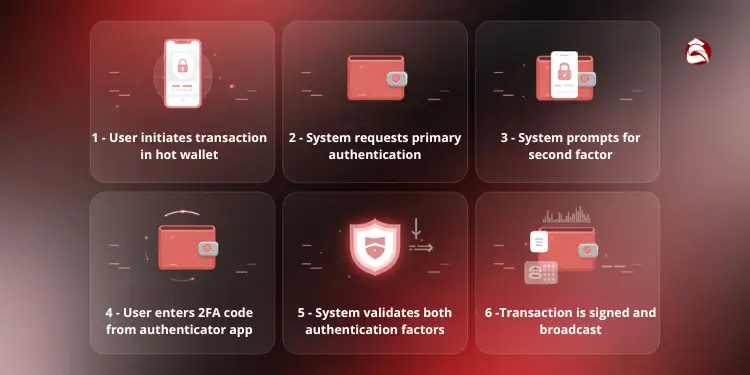
| Step | Action | Purpose |
|---|---|---|
| 1 | User initiates transaction in hot wallet | Starts the transfer process requiring authorization |
| 2 | System requests primary authentication | Verifies user identity with password/PIN |
| 3 | System prompts for second factor | Requests additional verification code |
| 4 | User enters 2FA code from authenticator app/SMS | Provides time-sensitive verification |
| 5 | System validates both authentication factors | Confirms legitimate user authorization |
| 6 | Transaction is signed and broadcast | Completes the secure transfer process |
Sending and receiving assets stepwise walkthrough
A hot wallet follows a straightforward process that enables quick transactions while maintaining security. This step-by-step walkthrough guides you through the essential procedures for both transferring funds to others and receiving payments into your hot wallet.
Sending Cryptocurrency Assets
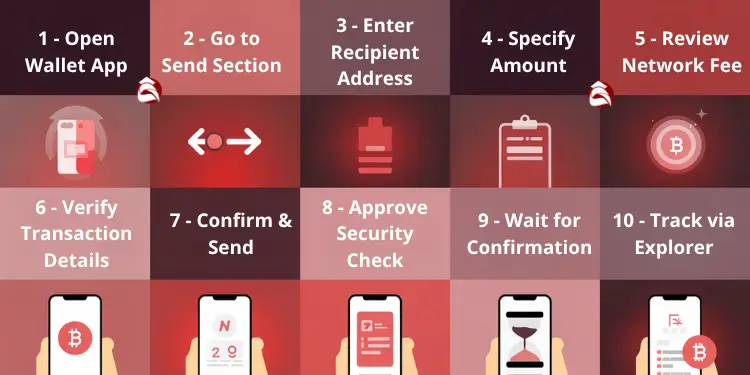
- Open hot wallet application and ensure connected to the internet.
- Navigate to the “Send” or “Transfer” section of your wallet interface.
- Enter the recipient’s cryptocurrency address accurately (double-check for errors).
- Specify the amount of cryptocurrency to send.
- Review the network fee (gas fee) and adjust if necessary for faster processing.
- Verify all transaction details, including the recipient address and amount.
- Click “Send” or “Confirm” to initiate the transaction.
- Approve any additional security measures (2FA, biometric verification, etc.).
- Wait for transaction confirmation on the blockchain (typically a few minutes to an hour) .
- Check your transaction status using a blockchain explorer if needed.
Receiving Cryptocurrency Assets
- Open your hot wallet application and navigate to the “Receive” section.
- Select the type of cryptocurrency you want to receive.
- Your wallet will display your public address (usually as a QR code and text).
- Share this address with the sender (you can copy the address or show the QR code).
- Wait for the sender to initiate and complete the transaction.
- Monitor your wallet for incoming transaction notifications.
- Once received, verify the transaction details and amount.
- Wait for required network confirmations (varies by cryptocurrency) .
- The received funds will appear in your wallet balance after confirmation.
- You can now use or transfer these funds as needed.
Migrating funds between hot and cold
Migrating funds between hot and cold wallets is a common practice for managing crypto assets securely, allowing users to balance accessibility with protection. The general recommendation is to keep only a small amount of cryptocurrency in your hot wallet for daily transactions while storing larger holdings in a cold wallet for long-term security.
- Transfer only necessary amounts to your hot wallet for immediate use.
- Keep the majority of your cryptocurrency holdings in cold storage for enhanced security.
- connect your cold wallet, generate a transaction to your hot wallet address, and confirm the transfer.
- initiate a send transaction from your hot wallet to your cold wallet’s public address.
- Always double-check recipient addresses before confirming any transfer.
- Consider network fees when timing your migrations between wallets.
- Wait for blockchain confirmations before considering the transfer complete.
- Maintain records of all transfers between your hot and cold wallets for accounting purposes.
“read also: How to verify blockchain transaction check transfers on chain“
Steps to Create a Hot Wallet
- Steps to Create a Hot Wallet:
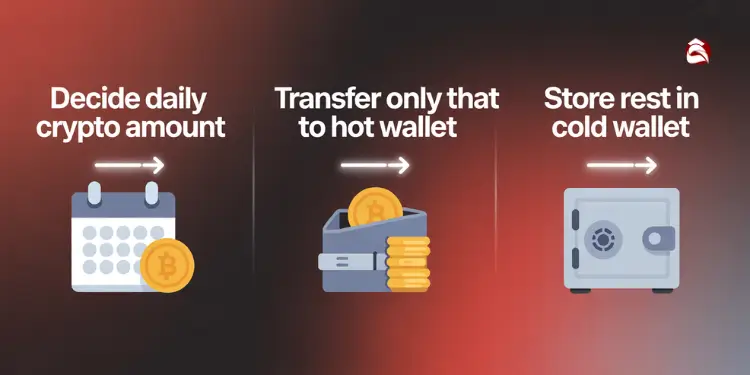
- Decide daily crypto amount.
- Transfer only that to hot.
- Store rest in cold wallet.
- Cold to Hot Transfer:
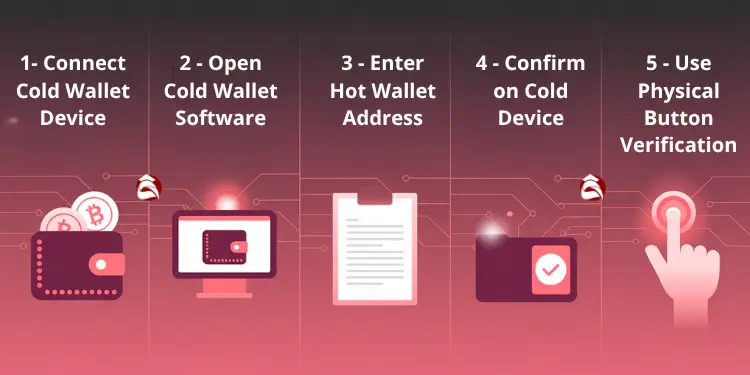
- Connect cold wallet device.
- Open cold wallet software.
- Enter hot wallet address.
- Confirm on cold device.
- Use physical button verification.
- Hot to Cold Transfer:
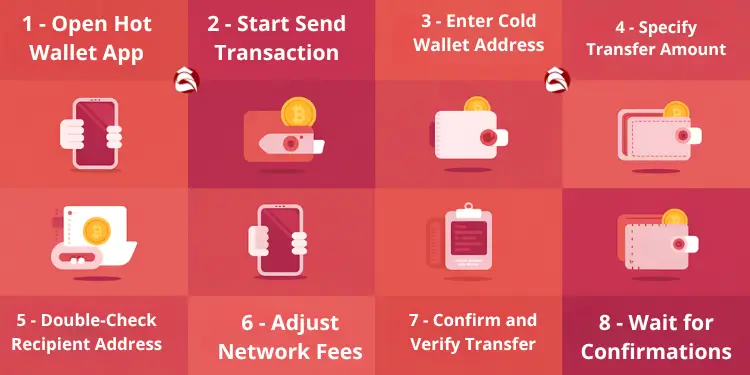
- Open hot wallet app.
- Start a send transaction.
- Enter cold wallet address.
- Specify transfer amount.
- Double-check recipient address.
- Adjust for network fees.
- Confirm and verify transfer.
- Wait for confirmations.
- Record all transfer details.
“Read Also: What is a blockchain block explained simply“
How Hot Wallets Facilitate Daily Transactions
Hot wallets play a significant role in facilitating daily crypto transactions due to their convenience and ease of use. These hot wallets offer quick access to your crypto, making it simple to send and receive payments for everyday purchases. Whether you are paying for a coffee, buying online goods, or sending cryptocurrency to a friend, hot wallets streamline the process.
Advantages and Disadvantages of Using Hot Wallets
Hot wallets offer distinct benefits and drawbacks that users must carefully consider when managing their cryptocurrency assets.
| Advantages | Disadvantages |
|---|---|
| Convenience and ease of use for everyday transactions | Increased security risk due to internet connectivity |
| Quick access to funds for immediate use | Vulnerable to hacking and phishing attempts |
| User-friendly interfaces suitable for beginners | Less secure than cold storage solutions |
| Real-time transaction processing and confirmations | Potential for unauthorized access if device is compromised |
| Integration with exchanges and DeFi platforms | Higher risk of loss compared to offline storage methods |
| No additional hardware costs required | Requires constant vigilance and security updates |
| Mobile accessibility for on-the-go transactions | Exposure to malware and keyloggers on connected devices |
Read More:
Hot wallets offer essential convenience for everyday crypto transactions while requiring careful security practices. By balancing accessibility with protective measures, users can safely manage digital assets for daily use. Strategic combination with cold storage provides the optimal approach for comprehensive cryptocurrency management.
A hot wallet works by storing encrypted private keys on an internet-connected device or application, allowing users to initiate transactions by entering recipient details and amounts. The wallet then uses the private key to generate a digital signature, broadcasts the signed transaction to the blockchain network, and awaits network verification and inclusion in a block. Once confirmed, balances are updated, completing the transfer process in seconds to minutes.
- Maintains constant internet connectivity for immediate access to funds
- Employs encryption, secure enclaves, and multi-factor authentication for security
- Facilitates real-time transactions but is inherently more vulnerable to online threats
- Typically holds only operational funds, with larger assets kept in cold storage
- Supports integration with exchanges and DeFi platforms for enhanced functionality
- Requires regular security updates and vigilant monitoring to mitigate risks












